 Back
Back
Frequently Asked Security Questions
This is our security FAQ page. We'll keep this page updated with new information as needed.
Questions answered here:
- How is my data stored?
- Who can see my data?
- Do you train on my data?
- Are my app connections secure?
- How do you pull my data?
- What measures are taken to prevent data leaks?
How is my data stored?
Infrastructure
camelAI’s infrastructure is hosted on AWS. Data from your connected applications are pulled only when you are chatting with camelAI and are limited to what you request in your prompt. We never access your accounts without your knowledge.
Conversation history, including the data you’ve requested, is stored in an EC2 cache for 5 minutes and then deleted.
Conversation History
Your conversation history is also stored on our servers so you can see your past conversations.
You can delete your conversations at any time in Account Settings by logging into camelAI > clicking on your user icon in the top left > clicking “Settings” > then “Clear History”. Clearing your history permanently deletes all of your conversations and your message level feedback (thumbs down, thumbs up, etc.).
App connections
Your connections, including connection strings, authorization tokens and API keys, are stored on our servers. They are never shared with our LLM provider and are encrypted in transit and at rest.
You can delete an app connection at any time in the Manage tab by logging into camelAI > clicking Manage in the side nav > clicking “Active” to show the active app connections > clicking the “...” button next to the app you would like to disconnect from > then press disconnect.
Who can see my data?
To answer this question, I’m going to explain our infrastructure. I’ll be referencing this image below to walk you through everything:
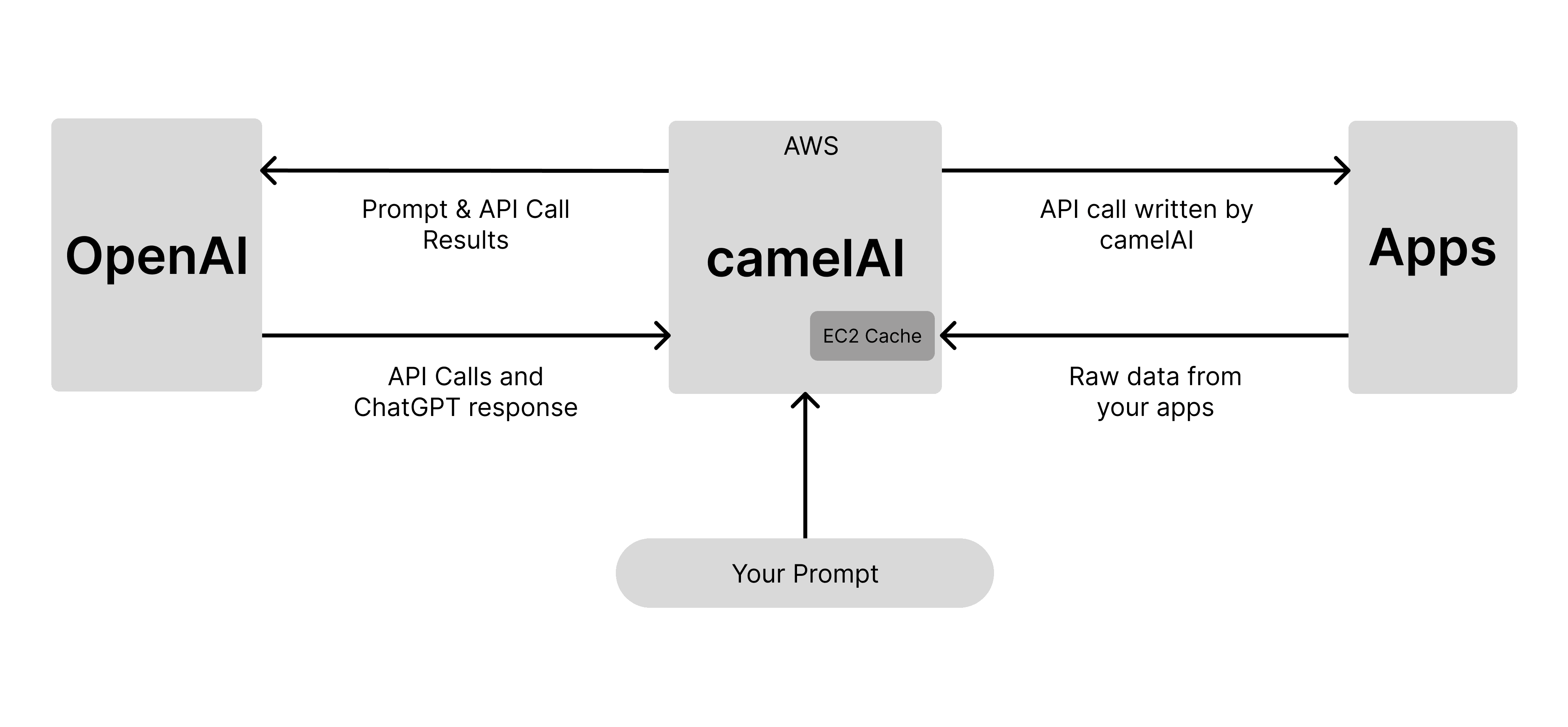
Your Prompt
To activate camelAI, you must send a message through the chat interface. No data pulls or actions occur without your knowledge.
camelAI
Your prompt, along with camelAI’s custom functions, are sent to our LLM provider. camelAI has proprietary functions that we maintain to allow an LLM to communicate with your desired application.
LLM provider (OpenAI or Anthropic)
The LLM provider receives the message and processes your command. This triggers a series of messages between the LLM provider and camelAI servers. These messages include chat output, function calls from the LLM to retrieve your data, and raw data output from your app connections for the LLM to process.
Apps
Your connected application receives API calls directly from camelAI’s servers. This is the only time camelAI communicates with your application. No queries are made without your knowledge. API calls to your application returns raw data, which is stored temporarily in our AWS EC2 Cache for 5 minutes before being cleared.
This process is subject to change. Be sure to check back for updates.
Do you train on my data?
No, we do not train on your data. CamelAI is powered by OpenAI's API. We have opted out of data sharing for training. You can read more about OpenAI's API policies here.
Are my app connections secure?
Yes, your app connections are secure.
We use OAuth 2.0 when available or secure key authentication to authenticate and authorize access to your applications. Your connections, including connection strings, authorization tokens and API keys, are stored on our servers. They are never shared with our LLM provider and are encrypted in transit and at rest.
If you revoke access to an app, the connection is immediately destroyed and we will no longer have access to that application.
How do you pull my data?
camelAI only communicates with your connected apps when you request data in the chat. We do not train on your data, nor do we access or store any data without your request and supervision.
Your connected application receives API calls directly from camelAI’s servers. This is the only time camelAI communicates with your application. No queries are made without your explicit request. API calls to your application returns raw data, which is stored temporarily in our AWS EC2 Cache for 5 minutes before being cleared.
What measures are taken to prevent data leaks?
We’re taking extensive precautions to ensure your data is secure.
SOC 2 and CASA
CamelAI is CASA certified.
We are actively pursuing the following certifications:
-
SOC 2 Type 1
-
SOC 2 Type 2
Please check back for updates on our certifications.
Vulnerability Defense
camelAI actively protects our systems against data leaks and attacks. Let’s go over potential vulnerabilities and how we’re combating them:
Hacking
- CASA certification means we’ve passed a security review where a third party attempted a cross site scripting attack, supply chain attack, scanned for known common vulnerabilities and exposures (CVE), and audited our data encryption.
- Your data is encrypted at rest.
Vendor Weaknesses
-
We carefully vet our vendors. All vendors interacting with customer data are SOC 2 compliant and are industry leaders, including AWS, OpenAI, and Cloudflare.
-
We work closely with our vendors to comply with their terms of service and maintain good standing.
Can I control the connections and scope of camelAI’s access to each application?
Yes! During onboarding, you can configure various settings, including:
-
Determining read or read/write access
-
Selecting which org or project is visible to camelAI
-
Disconnecting immediately, which severs all communication between camelAI and your application
You can also email us to securely delete your entire account activity.
If you have any additional questions regarding security, please email us at [email protected].
Last updated September 30, 2024.


